
Ch.5 Combination Logic
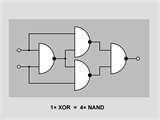
Information Security Lab. The NAND and NOR gate are universal gates because they can produce ANDs, ORs and NOTs.(Why use them?) Information Security Lab. program for the XOR OR circuit cont’d . architecture LogicOperation of XOR_OR_Logic is … Return Doc
Operations Algorithms On Quantum Computer
IJCSNS International Journal of Computer Science and Network Security, VOL.10 No.1, January 2010 85 Manuscript received January 5, 2010. Quantum Not and XOR Gates [8, 9, 10] The problem of universality can be posed for quantum computation as well, in asking whether arbitrary unitary … Access Full Source
Understanding AES Mix-Columns Transformation Calculation
(I am assuming you know the theory for XOR gates and some other simple theories) Let's take this example: In this example, our a 0 – a 3 is equals to d4 – 30 Rijndael_mix_columns [2] William Stalling (2006), Chapter 4.6 Finite Fields of the Form GF(2 n) – Multiplication, in Cryptography and Network Security … Fetch Here

Physical Unclonable Function And True Random Number Generator …
A representative design uses 32 3-inverter ring oscillators, 64 flip-flops/latches, 31 2-input XOR gates and control circuitry giving a 3.2Mbps truly In the light of increasingly compact single chip solutions, this architecture would be ideally suited for security device or trusted computing modules. … View This Document
Minecraft Logic Gates – YouTube
I finally got around how red stone works and decided to make some logic gates. xor; xnor; flip-flop; mine; craft; logic; gate; tutorial; and; or 1:04 Watch Later Error minecraft security door with lock by flexyque 183,967 views … View Video

Improved Garbled Circuit Building Blocks And Applications To …
(This technique was subsequently extended in the LEGO paper [NO09]which allows to compose garbled circuits dynamically with security against malicious circuit constructor). Clearly, the usage of such garbled values allows for free evaluation of XOR gates with input wires W 1,W 2 and output wire W 3 by … Retrieve Full Source
Boolean Operator – Boolean Algebra – Boolean Logic
A xor B This is asking for A or B but not both, to be true. Since they are both true, this expression is FALSE Security; PHP/MySQL Basics; Tools & Resoruces; Troubleshooting; Programing Glossary … Read Article
Publishable Executive Summary
Will be to look at header based signatures • Security applications to implement within photonic firewall are those that target known attacks: firewall operations and DoS prevention • Security applications will rely on 5 to 6 (growing to up to a dozen in the near future) optical gates performing XOR … Doc Viewer

FPGA DESIGNS OF PARALLEL HIGH PERFORMANCE GF(2^233) MULTIPLIERS
We have selected GF (2 233) to satisfy the security requirements in elliptic curve cryptography for the next years, but our results can be adapted to This struc-turerequires 28800 AND and 31183 XOR gates, and atotalpropa-gationdelayof T AND +14 T XOR. … Return Doc

Privacy Preserving Auctions And Mechanism Design
FK(x)| = |Wkbk|+1 The table contains four entries: For A to use the table A knows (Wibi,ci), (Wjbj,cj) Finds (ci,cj) in the table Performs XOR to output bits By the end of the oblivious transfer stages, A has enough information to compute f(x) Two-Party Secure Function Evaluation Security of gates … View Full Source
About Experts Sitemap – Group 169 – Page 8
Http://en.allexperts.com/q/C-1587/Logical-gates.htm http://en.allexperts.com/q/C-1587/XOR-store-byte.htm http://en.allexperts.com/q/C-1587/random-numbers-security.htm … Read Article
MIPS Architecture – Wikipedia, The Free Encyclopedia
The two are strongly related; the price of a CPU is generally related to the number of gates and Cavium, originally a security processor vendor also produced devices with eight CPU cores, and later xor $d,$s,$t $d = $s ^ $t: R: 0: 26 16: Nor: nor $d,$s,$t $d = ~ ($s | $t) … Read Article
PowerPoint Presentation
Thanks to Cadence Design Systems for the VLSI lab Thanks to Synopsys for Software donation Dr. David Parent Thanks to the janitors/security for EE-166) BGCC, is applied in many applications This project converts a series of binary numbers to gray code numbers with the use of XOR gates and … Read More
Bit-Parallel Word-Serial Finite Field Multiplier Over GF\(2233\)
7 Research Motivations •Smart card and applications-Usually a plastic card that contains a security processor and has many security related 21 Comparisons GF(2 m) GF(2 233) Finite field 8*233 AND gates 8*233 +36 XOR gates Two 233-bit registers 30 Alternative BPWS 8*233 AND gates 8*233+36 XOR gates one 233 … Fetch Full Source
